Enterprise networking is evolving rapidly to meet the demands of hybrid work, IoT expansion, and cloud-native operations.
Modern campus networks are no longer isolated infrastructures; they form part of an integrated digital fabric extending from user devices to multicloud and edge environments.
This article presents a ready roadmap for transforming legacy campus architectures into cloud-aligned, secure, and intelligent environments.
Foundations of the Modern Campus Fabric
Modern campus designs replace rigid three-tier models with fabric-based architectures that utilize EVPN/VXLAN overlays for enhanced scalability and segmentation. These fabrics enable dynamic traffic steering, consistent policy enforcement, and simplified operations.
Whether implemented through Cisco SD-Access, Aruba ESP, or Juniper Mist AI, the goal remains the same: provide identity-based segmentation, automation, and analytics across wired and wireless domains.
Key Principles:
- Unified Fabric: Consistent policy and segmentation from access to the border.
- Automation & API-first Control: Configuration-as-code using Ansible or Terraform.
- Resilient Underlay: Redundant Layer 3 uplinks with MACsec (802.1AE) for encrypted links.
- Multigigabit Uplinks: 802.3bz (2.5/5GBASE-T) and 10GBASE-T for high-throughput Wi-Fi 6/7 access points.
Wireless and Power Infrastructure
Wi-Fi 6E and Wi-Fi 7 offer unprecedented throughput and efficiency, but real-world client goodput typically ranges between 600–900 Mbps (80 MHz) and 1.5–2 Gbps (160–320 MHz). Plan for AP density, spectrum management, and backhaul capacity rather than PHY peak rates.
Power Considerations:
- Adopt IEEE 802.3bt (Type 3/4) PoE for up to 90W per port.
- Model power budgets per switch and PSU for dense IoT or camera deployments.
- Use UPS-backed power zones for mission-critical edge compute and AP clusters.
Zero Trust by Design
Zero Trust in the campus environment goes beyond segmentation. It integrates identity, posture, and continuous verification:
- Access Control: 802.1X with EAP-TLS for certificate-based authentication.
- Identity Policy: Dynamic VLANs or SGT/GBP-based micro-segmentation.
- Device Posture: Integration with MDM/UEM (Intune, Workspace ONE) and compliance enforcement.
- Traffic Protection: MACsec for wired, WPA3-Enterprise for wireless, and TLS 1.3 for application flows.
- Visibility: Real-time telemetry streaming to SIEM or SOAR for anomaly detection.
Cloud Connectivity and Data Flow Accuracy
Campus networks must integrate seamlessly with SASE/SSE frameworks for secure cloud access. Traffic flow should be explicitly routed through SD-WAN edges or cloud security brokers:
Example Flow: User Device → Access Point → Fabric Edge → Border Node → SD-WAN Edge → SSE Gateway → SaaS/IaaS Cloud
Best Practices:
- Prefer Direct Connect, ExpressRoute, or Cloud Interconnect for deterministic performance.
- Avoid Layer 2 extensions into the cloud; adopt routed overlays.
- Apply DNS filtering, DLP, and ZTNA at the SASE layer.
Automation, AIOps, and Observability
AIOps platforms (Cisco DNA Center AI Analytics, Juniper Mist AI, Aruba Central) provide valuable insights, but should be framed realistically:
- Anomaly Detection – Highlight deviations from historical baselines.
- RRM Optimization – Suggest channel/power changes based on interference.
- Root Cause Analysis (RCA) – Correlate events across domains.
Integrate telemetry with ITSM (ServiceNow, Jira) and CMDB systems via REST APIs or webhooks for closed-loop automation.
Migration Roadmap for Legacy Campuses
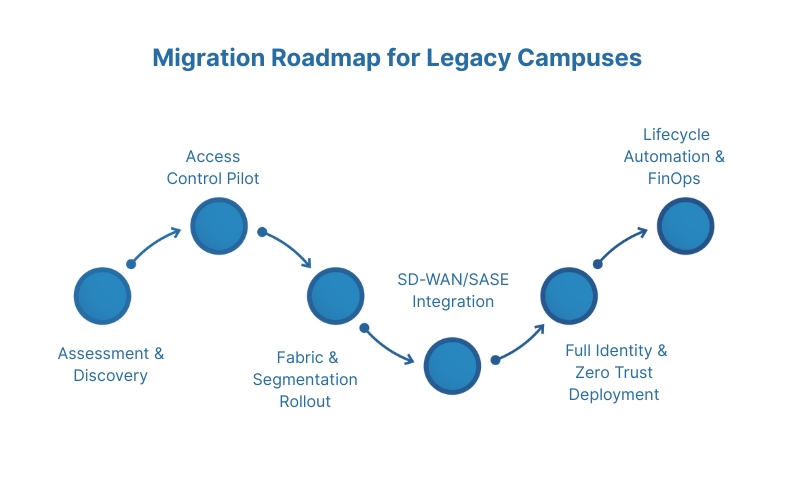
Phase 1: Assessment & Discovery
- Inventory hardware, firmware, and licenses.
- Capture telemetry and utilization baselines.
Phase 2: Access Control Pilot
- Deploy 802.1X with EAP-TLS in a single site.
- Validate identity and posture enforcement.
Phase 3: Fabric & Segmentation Rollout
- Introduce EVPN/VXLAN or SD-Access fabric overlays in select buildings.
- Gradually replace VLAN-based isolation with group-based policy.
Phase 4: SD-WAN/SASE Integration
- Migrate cloud egress to SSE gateways.
- Define application-aware routing and split-tunnel policies.
Phase 5: Full Identity & Zero Trust Deployment
- Expand certificate enrollment automation (SCEP/EST/ACME).
- Enforce device posture and continuous verification globally.
Phase 6: Lifecycle Automation & FinOps
- Adopt image catalogs, staged upgrades, and compliance reporting.
- Implement FinOps practices for license tiers, cloud egress, and energy consumption.
Emerging Technologies and Future Alignment
Containerized Edge & Hybrid Control:
- Integrate Anthos, Azure Arc, or GKE Anywhere for edge workload orchestration.
- Manage policies across cloud and on-prem Kubernetes clusters.
IoT and MEC Integration:
- Use MQTT brokers or lightweight service meshes for on-prem analytics.
- Isolate IoT via dynamic segmentation and MACsec.
Lifecycle Security:
- Automated certificate renewal, RADIUS/IdP redundancy, and firmware governance aligned to CIS/STIG baselines.
Conclusion
The modern campus network functions as an intelligent, secure extension of the multicloud environment. Success requires aligning Zero Trust, AIOps, and fabric automation under a unified architecture, while managing costs and compliance through FinOps.
The enterprises that adopt these principles will achieve not just connectivity, but a secure, cloud-aligned digital edge ready for the next decade of transformation.







